What is LoRaWAN
As the scale of the Internet of Things continues to expand and its applications become more extensive, there are more and more access control points, and the use of LoRaWAN has become a trend. What is LoRaWAN? This article will give an introductory technical overview of LoRaWAN to help LoRa practitioners understand LoRaWAN in an all-around way.
1. What is LoRaWAN
LoRaWAN is a set of communication protocols and system architecture designed for a LoRa long-distance communication network. It defines how data is transmitted in the LoRaWAN network (the network here refers to nodes, gateways, and servers), defines the message type, data frame structure, and security encryption method; and introduces the specific operations of the network, and explains The difference between master and slave.
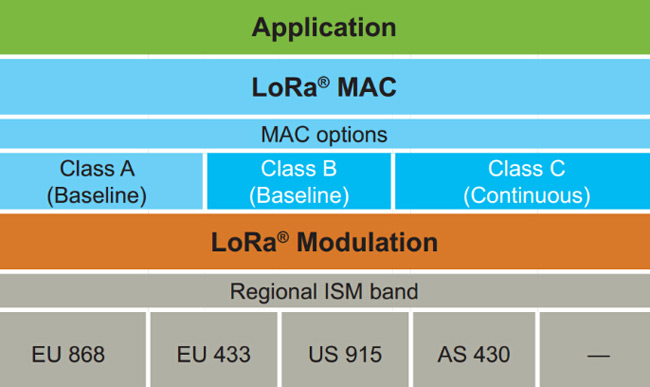
Protocol hierarchy diagram
In the design of the protocol and network architecture, LoRaWAN fully considers several factors such as node power consumption, network capacity, QoS, security, and network application diversity.
2. LoRaWAN network architecture
Let's do some understanding from a technical point of view. The following is the network architecture diagram in the official white paper of the LoRa Alliance.
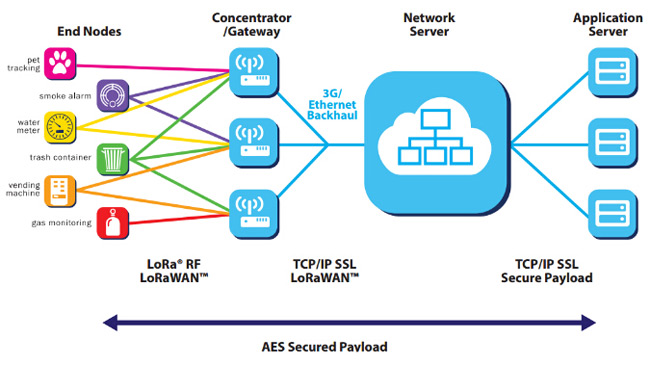
It can be seen that a LoRaWAN network architecture includes four parts: terminal, base station, NS (network server), and application server. A star network topology is adopted between the base station and the terminal. Due to the long-distance characteristics of LoRa, single-hop transmission can be used between them. In the terminal section, there are 6 typical applications listed. There is a detail. You will find that the terminal node can send to multiple base stations at the same time. The base station forwards the LoRaWAN protocol data between the NS and the terminal and carries the LoRaWAN data on the LoRa radio frequency transmission and TCP/IP respectively.
Let's take a look at this network architecture in conjunction with the industry ecology below, and everyone can have a deeper understanding.
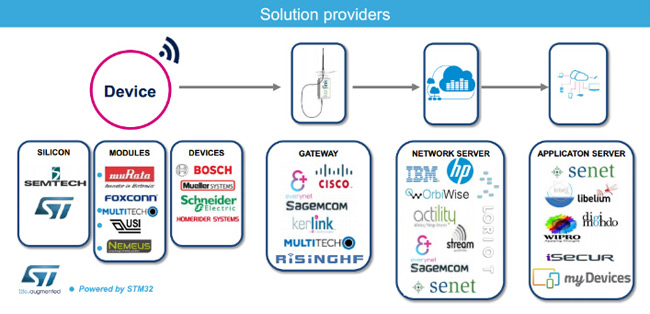
3. Overview of the agreement
- Classification of terminal nodes
In the introduction at the beginning, we saw that there are three types of terminal equipment specified in the agreement, Class A/B/C, and these three types of equipment basically cover all the application scenarios of the Internet of Things. For your convenience, a table is made.
| CLASS | introduction | Downside timing | Application scenario |
| A(“all”) | Class A terminals use the ALOHA protocol to report data on demand. After each uplink, two short downlinks receive windows will be followed to achieve two-way transmission. This kind of operation is the most energy-efficient. | You must wait for the terminal to report data before sending data to it. | Trash can monitoring, smoke alarm, gas monitoring, etc. |
| B(“beacon”) | In addition to the random receiving window of Class A, the terminal of Class B will open the receiving window at the specified time. For the terminal to open the receiving window within a specified time, the terminal needs to receive a time-synchronized beacon from the gateway. | Data can be delivered to the terminal in a fixed receiving window, and the delivery delay is increased. | Valve-controlled water gas meter |
| C(“continuous”) | The Class C terminal basically keeps the receiving window open all the time, and only closes it briefly when sending. Class C terminals consume more power than Class A and Class B. | Since the terminal is in a continuous receiving state, data can be sent to the terminal at any time. | Street lamp control, etc. |
- Uplink and downlink transmission of terminal nodes
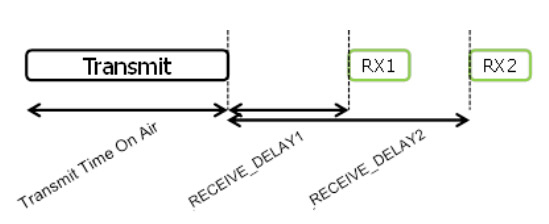
This is the sequence diagram of Class A uplink and downlink. At present, the receiving window RX1 generally starts 1 second after the uplink, and the receiving window RX2 starts 2 seconds after the uplink.
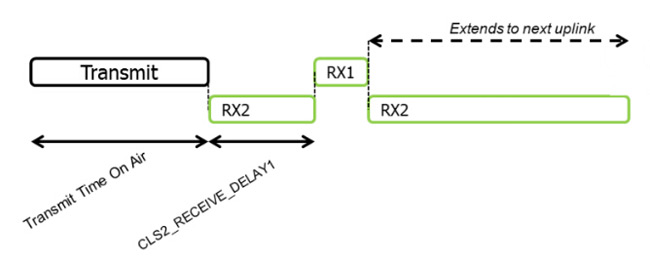
Class C and A are basically the same, except that when Class A is sleeping, it opens the receiving window RX2.
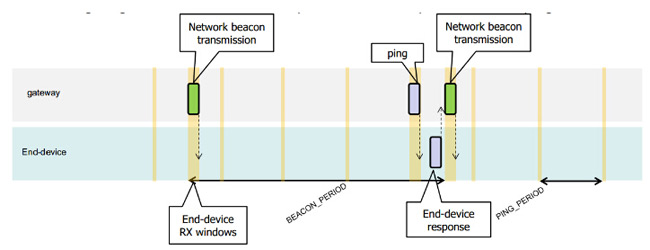
The time slot of Class B is more complicated. It has a synchronous time slot beacon and a fixed-period receiving window ping time slot. In this example, the beacon period is 128 seconds, and the ping period is 32 seconds.
- Screening of terminal nodes
After understanding the basic concepts, you can understand how nodes work. Before officially sending and receiving data, the terminal must first add to the network.
There are two screening methods: Over-the-Air Activation (OTAA) and Activation by Personalization (ABP).
Commercial LoRaWAN networks generally follow the OTAA activation process, so that security can be guaranteed. This method needs to prepare the three parameters DevEUI, AppEUI, and AppKey.
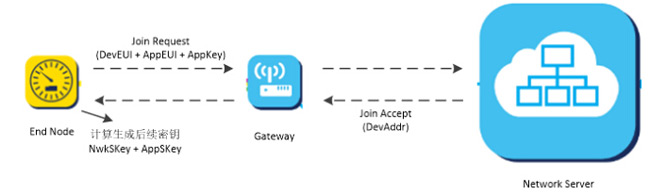
DevEUI is a globally unique ID similar to IEEE EUI64, which identifies a unique terminal device. It is equivalent to the MAC address of the device.
AppEUI is a globally unique ID similar to IEEE EUI64, which identifies a unique application provider. For example, each trash can monitoring application, a smoke alarm application, etc., all have their own unique ID.
AppKey is assigned to the terminal by the owner of the application.
After the terminal initiates the network join process, it sends a network addition command. After the NS (network server) confirms that it is correct, it will respond to the terminal and assign the network address DevAddr (32-bit ID). Both parties use the relevant information in the network response and AppKey generates session keys NwkSKey and AppSKey, which are used to encrypt and verify data.
If the second screening method is used, that is, ABP activation, it is relatively simple and rude. Directly configure the three LoRaWAN final communication parameters, DevAddr, NwkSKey, and AppSKey. The join process is no longer required. In this case, the device can send application data directly.
- Data sending and receiving
After adding the network, the application data is encrypted.
LoRaWAN stipulates that there are two types of data frames: Confirmed or Unconfirmed, that is, the type that requires a response and the type that does not require a response. The manufacturer can choose the appropriate type according to the application's needs.
In addition, it can be seen from the introduction that a major consideration at the beginning of LoRaWAN design is to support application diversity. In addition to using AppEUI to divide applications, the FPort application port can also be used to process data separately during transmission. The value range of FPort is (1~223), which is specified by the application layer.
- ADR mechanism
We know that there is a concept of spreading factor in LoRa modulation. Different spreading factors will have different transmission distances and transmission rates, and they will not affect each other's data transmission.
To expand the LoRaWAN network capacity, a LoRa rate adaptation (Adaptive data rate-ADR) mechanism is designed in the protocol. Devices with different transmission distances will use the fastest data rate possible according to the transmission conditions. This also makes the overall data transmission more efficient.
- MAC commands
Aiming at the needs of network management, a series of MAC commands are designed on the protocol to modify the relevant parameters of the network. For example, the delay of the receiving window, the device rate, and so on. In the actual application process, it is generally rarely involved and temporarily ignored.
The above is the basic overview of LoRaWAN. I believe everyone should have a deeper understanding of LoRaWAN. In the next few years, various fields of the Internet of Things will be widely used in LoRaWAN, and some new problems may also be encountered in actual projects. But this is just a process. If you want to save trouble, you can use the LoRaWAN serial modules developed by some LoRa module manufacturers. These modules provide simple serial AT commands, which are very convenient to use.
 +86-755-23080616
+86-755-23080616
 sales@nicerf.com
sales@nicerf.com
Website: https://www.nicerf.com/
Address: 309-314, 3/F, Bldg A, Hongdu business building, Zone 43, Baoan Dist, Shenzhen, China